OTP & Authentication
Sep 4, 2024
The simple guide to understand TOTP and HOTP
In today's digital world, security is a top priority. We've all heard about traditional passwords and how they aren't as secure as we once thought. This is where one-time passwords (OTPs) come in. They offer a more secure and dynamic way of authenticating users.
Today, we'll dive into two popular OTP methods: Time-Based One-Time Password (TOTP) and HMAC-Based One-Time Password (HOTP). What are the differences between them? And how do you decide which one best suits your needs? Let's dive in.
Understanding OTP
First things first, what exactly is an OTP?
An OTP is a unique password that can only be used once for a single login session or transaction. These passwords are usually six digits long and are used in Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA) systems.
The main advantage of OTPs is that they are dynamic and short-lived, making them much more secure than static passwords. For more information, you can read our full guide on SMS OTP.
Now, let's dive into the two main types of OTPs.
Time-Based One-Time Password (TOTP)
How does TOTP work?
TOTP uses a time-based algorithm where the moving factor is the current Unix time divided by a timestep value, typically set at 30 or 60 seconds. This means that the OTP is only valid for a short period, enhancing security.
The TOTP algorithm typically works as follows:
A shared secret is established between the server and the client.
The current time is determined and divided by the timestep.
This value is combined with the shared secret using a cryptographic hash function.
The resulting hash is truncated to create a human-readable OTP.
TOTP Benefits and Drawbacks
✅ Benefits:
Higher security due to short validity period
Reduces the window for potential attacks
Self-synchronizing (based on current time)
🚩 Drawbacks:
Requires time synchronization between user's device and server
OTP can expire before entry, which might be inconvenient
Sensitive to time drift on devices
HMAC-Based One-Time Password (HOTP)
How does HOTP work?
HOTP relies on an event-based algorithm. When the user requests an OTP, a counter increments on both the client and server sides. This counter, along with a shared secret key (known as the "seed"), generates a unique OTP. This process uses the HMAC-SHA-1 hashing function.
The HOTP algorithm typically works as follows:
A shared secret and initial counter value are established between the server and client.
When an OTP is requested, the current counter value is combined with the shared secret using HMAC-SHA-1.
The resulting hash is truncated to create a human-readable OTP.
The counter is incremented on both sides after use.
HOTP Benefits and Drawbacks
✅ Benefits:
Flexible, as OTP doesn't expire until used
No time synchronization required
Can be implemented offline
🚩 Drawbacks:
Potentially less secure due to longer validity period
Risk of desynchronization if multiple OTPs are generated without use
Requires secure counter management on both client and server sides
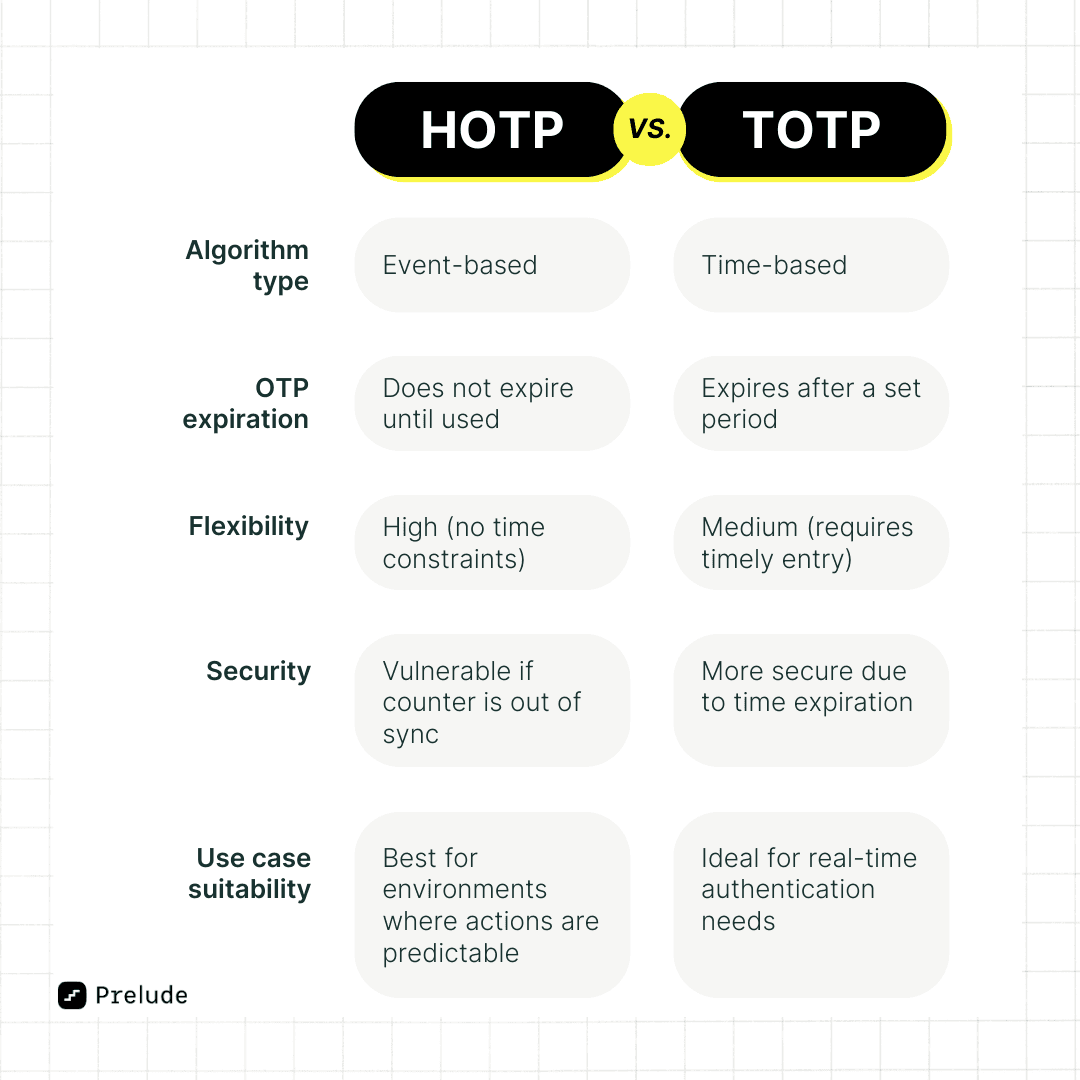
Key differences between HOTP and TOTP
⏳ OTP Expiration
One of the main differences is how long the OTP remains valid. HOTP tokens do not expire until used, which gives you more flexibility. On the other hand, TOTP tokens expire after a set period, usually 30-60 seconds, which enhances security but requires timely entry.
🔐 Convenience vs. Security
HOTP offers a more user-friendly experience without time constraints but is less secure due to the validation window vulnerability. TOTP, while requiring timely entry of the OTP, is more secure because of its time-based expiration.
🪢 Implementation Complexity
HOTP is generally easier to implement because it doesn't require time synchronization. TOTP, however, needs accurate time synchronization, adding a layer of complexity but also increasing security.
Choosing between HOTP and TOTP
Your choice between HOTP and TOTP depends on your specific needs and circumstances:
Security Requirements: If a secure OTP system is your top priority, TOTP is generally the better choice.
User Experience: If you want to avoid time constraints for users, HOTP might be more suitable.
Time Synchronization: If keeping devices synchronized is a challenge, HOTP can be a more practical option.
Resources and Implementation: If you're looking for something quick and easy to implement with fewer resources, HOTP is the way to go.
Online vs. Offline Use: For offline applications, HOTP might be more suitable as it doesn't require real-time server communication.
Both HOTP and TOTP significantly improve security over traditional passwords by offering dynamic, one-time use authentication methods.
TOTP's time-based nature makes it generally more secure, making it the preferred choice for most modern online applications.
When choosing between HOTP and TOTP, consider your specific security requirements, user experience goals, and implementation constraints. Whichever method you choose, implementing robust OTP systems can significantly enhance your security posture, protecting your digital assets from unauthorized access and ensuring a safer user experience.
Looking to implement secure OTP solutions for your application?
At Prelude.so, we specialize in providing advanced TOTP SMS verification and mobile onboarding infrastructure through a set of unified APIs.
Our solution allows companies to:
Verify their users globally across multiple channels: SMS, WhatsApp, Viber or RCS
Prevent SMS pumping fraud to protect their users (and their budget)
Get started with user verification in less than a day, with user-friendly APIs and comprehensive documentation
Reduce their verification budget through competitive pricing and transparent billing
We also have a guide where we compare the top 10 SMS API provider in the market.
Whether you're in social media, dating, fintech, e-commerce, or any other industry requiring user verification, Prelude.so can help you streamline your authentication processes and boost security.



