Security Tips
Jan 7, 2025
If your app uses phone verification, you will most likely be a victim of SMS Pumping Fraud. Here's everything you need to know about it.
SMS verification is essential for businesses today, from securing accounts to preventing fraud. But what happens when SMS becomes the very tool scammers use to drain your resources? Enter SMS pumping fraud, a sophisticated scam that’s costing companies millions each year.
In this guide, we’ll break down what SMS pumping fraud is, how it works, and most importantly, how to protect your business from this growing threat.
What is SMS pumping fraud?
SMS pumping is a type of scam where fraudsters generate fake text messages to premium-rate numbers they control to earn money. They either trick people into sending these messages or exploit digital services like OTPs (one-time passwords) to trigger automated SMS traffic.
Fraudsters often work with unethical mobile operators or find ways to hijack SMS routes to drive this fake traffic. Since businesses pay for each SMS they send and customers can unknowingly rack up charges to premium numbers, the financial damage can be significant.
Also known as SMS Toll Fraud or Artificially Inflated Traffic (AIT), SMS pumping is a form of International Revenue Sharing Fraud (IRSF) that impacts both businesses and individuals, with companies facing the biggest financial losses.
How does SMS pumping work?
SMS pumping is a sophisticated scam that requires technical expertise and often the involvement of a mobile network operator, whether knowingly or unknowingly.
Fraudsters start by partnering with unethical carriers or gaining access to premium-rate numbers. They promise these operators high SMS volumes and increased revenue, using international premium-rate numbers (IPRNs) to drive traffic.
Once the carrier agrees, the fraudsters flood the system with SMS traffic, typically through digital triggers like OTP requests, account verifications, or two-factor authentication (2FA) codes.
These SMS messages are routed to premium numbers controlled by the fraudsters, usually in foreign countries, inflating the cost for businesses that pay per message. When the victim (a business or individual) receives the inflated bill, the carrier splits the revenue with the fraudsters who orchestrated the attack.
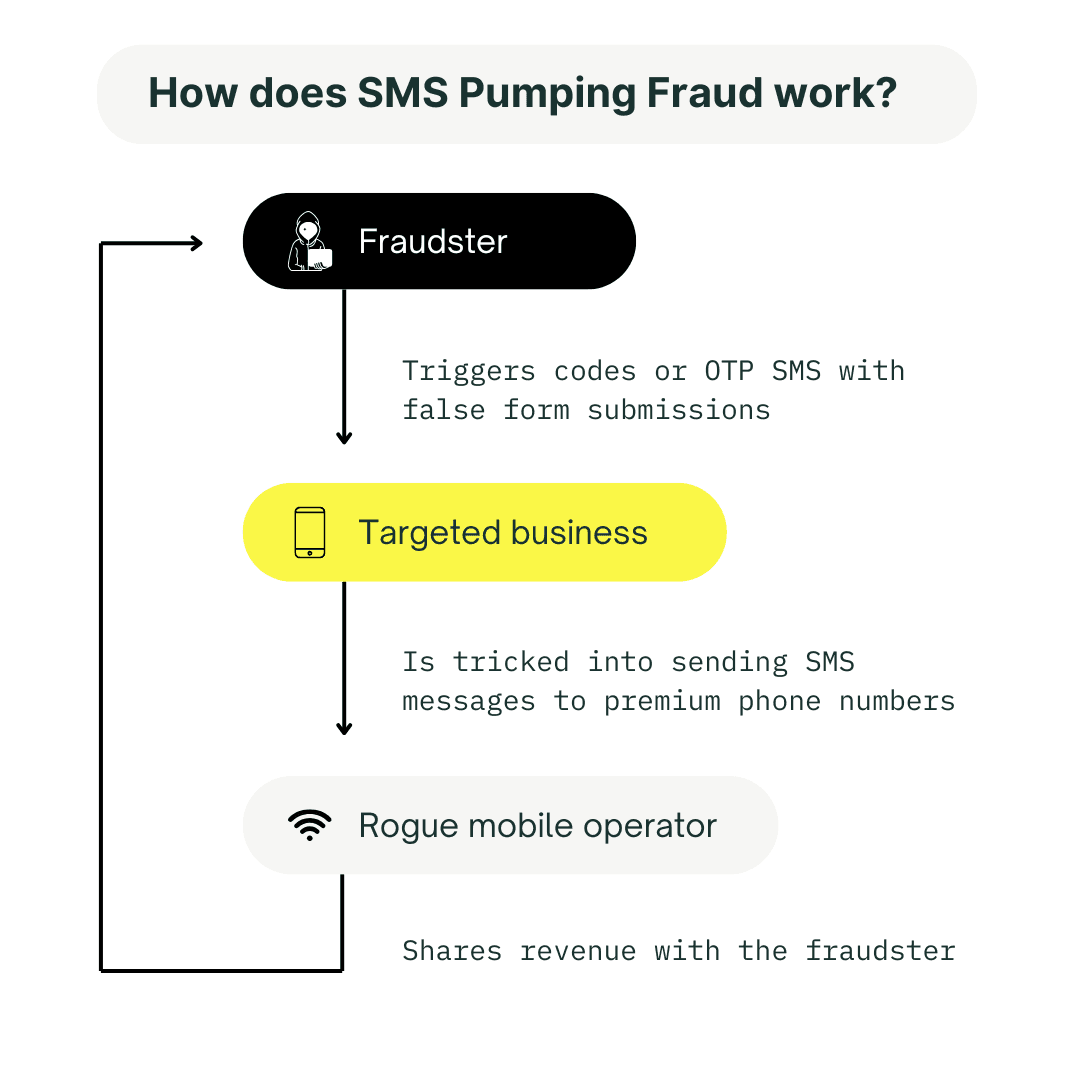
In short, both the scammers and their rogue partners profit from the fake SMS traffic, while the victim is left covering the costs.
Examples of SMS pumping fraud
Targeting an individual
Lily receives an SMS that says: “Congratulations! You've won a $100 gift card! Reply 'YES' to claim.”
Excited by the offer, Lily replies “YES.” What she doesn’t know is that by replying, she has unknowingly subscribed to a premium SMS service.
Suddenly, Lily starts receiving frequent messages from a premium-rate number, and she’s being charged for every text received. Her phone bill skyrockets, but she only realizes something is wrong when she sees the unexpected charges.
Trying to cancel the subscription is a nightmare. She’s forced to jump through hoops: sending more messages (which also cost money), navigating poorly designed websites, or contacting hard-to-reach customer service numbers.
Targeting a company
DopeSocks, a subscription-based luxury clothing retailer, offers customers 15% off their first subscription in exchange for entering their phone number on the website.
Once a customer enters their phone number, the company sends an SMS with a discount code. It’s a simple strategy to boost signups from interested customers.
But fraudsters see an opportunity. They use bots to flood the website with thousands of fake phone numbers. Each number triggers an SMS that is routed to a premium-rate number controlled by the scammers.
DopeSocks ends up with a huge bill for all those SMS messages — but no real customers. Every text they sent went to fraudulent numbers, benefiting the scammers while leaving the company to foot the bill.
When these messages are sent, they bounce from network to network before reaching their destination. That means there’s no way to detect which network is colluding with the authors of the SMS fraud. In most cases, you never identify the criminal who defrauded your system.
How SMS pumping fraud hurts businesses
In 2023, 5% of Application-to-Person (A2P) SMS were fraudulent. This means more than 20 billion messages were sent by fraudsters! These fraudulent messages cost brands a staggering $6.7 billion globally (source).

Even the biggest names with huge engineering budgets are not immune to it. For instance, Elon Musk reported that Twitter was getting scammed by phone companies for $60M/year of fake 2FA SMS messages.
SMS fraud is widespread and can impact businesses in many ways:
1. Immediate financial loss
This one is the most obvious. Fraudulent SMS traffic leads to massive financial hits. Since businesses pay for every SMS they send, scammers can exploit this to drive up costs by routing messages to premium numbers they control.
These costs can quickly add up to hundreds of thousands, or even millions. Worse still, if employees or customers fall victim to SMS scams, businesses may be forced to cover the fraudulent charges, creating unexpected and devastating financial liabilities.
That’s why having strong promotion abuse prevention tools in place, like real-time monitoring and automatic blocking, is essential to protect both your users and your budget.
2. Compromised security and privacy
SMS pumping doesn’t just impact your budget, it also jeopardizes security and privacy. Fraudsters often use tactics like SIM swapping, phishing, or smishing to gain unauthorized access to sensitive customer data.
When a business fails to protect this information, the consequences are severe:
Customer identity theft
Unauthorized access to company accounts
Violations of privacy regulations (like GDPR)
Loss of intellectual property
Let’s face it: no brand can survive a reputation for poor security, especially in an era where digital privacy concerns are at an all-time high.
3. Lower conversion rates
At first, it might seem like you’re gaining a flood of new users, but don’t be fooled. If your company is targeted by an SMS pumping attack, those signups are fake accounts created by bots — users who will never convert into paying customers.
Your user base gets inflated with fake profiles. Your conversion rate plummets while your cost per conversion skyrockets, making it harder to justify marketing spend. Your reporting and analytics become unreliable, and bad data leads to bad decisions.
In short, fake traffic poisons your performance metrics and makes it impossible to gauge true customer behavior. Without accurate data, your marketing and sales strategies suffer, and you end up wasting time, money, and resources chasing ghosts.
4. Saturation of communication channels
When fraudsters flood your SMS traffic, it's like an all-you-can-eat buffet for bots. And your real users are left starving.
A large-scale SMS pumping attack overwhelms your messaging system, clogging it with fake traffic. Your SMS provider gets overloaded, causing delays or even total service interruptions.
Real users can’t receive critical messages, whether it’s a login code, a payment confirmation, or a password reset. Customers trying to validate their online purchases or financial transactions are left in the dark.
The result? Frustrated users, abandoned carts, and dwindling trust in your brand. Worse, these delays often hit at the worst times, like peak shopping seasons or crucial app updates.
5. Erosion of brand reputation
Fraud doesn’t just hurt your bottom line, it destroys trust. Whether it's customers or employees, once trust is broken, it’s incredibly difficult to rebuild.
Customers will stop buying from businesses that can’t keep their data safe, and employees will feel vulnerable if their personal contact details are exposed to scammers. This leads to lost revenue, damaged brand credibility and a decline in customer loyalty and retention.
Put simply: trust takes years to build and seconds to lose. SMS pumping fraud is one of the quickest ways to dismantle your reputation.
6. Added operational costs
Dealing with the consequences of SMS pumping fraud doesn’t just eat into your financial resources. It will also make huge demands on your employees’ productivity because cybersecurity personnel will have their hands full fixing issues for every fraud victim.
They also have to investigate each fraudulent charge, manage justifiably irate customers, implement more robust security mechanisms for the future, and, if possible, trigger lawsuits against the fraudsters (if they can be identified).
How to detect SMS pumping fraud?
Fraud prevention is a never-ending game of cat and mouse, and SMS pumping fraud is no exception. However, there are clear warning signs that your business might be under attack. Here's what to look out for:
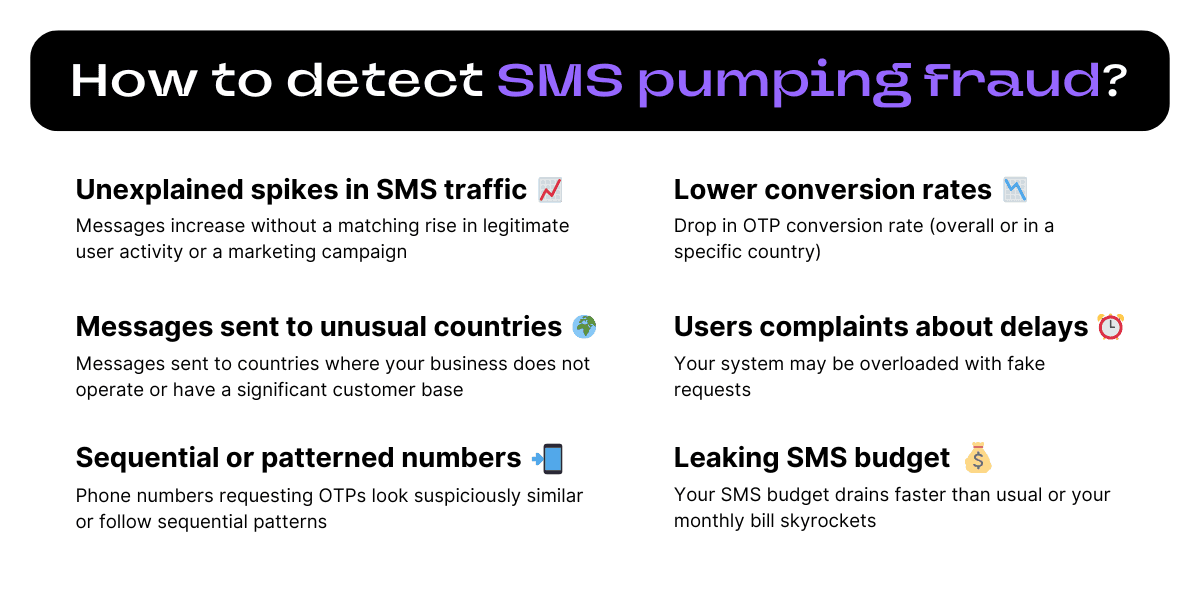
1. Unexplained spikes in SMS traffic
Notice a sudden surge in SMS traffic, especially outside of peak hours? That’s a red flag.
If your OTP requests or SMS messages increase without a matching rise in legitimate user activity or a marketing campaign, it’s likely that fraudsters are behind it.
2. SMS messages sent to unusual countries
If you notice a high volume of SMS messages being sent to countries where your business does not operate or have a significant customer base, it could be a sign of fraudsters exploiting your SMS services.
3. Sequential or patterned phone numbers
If the phone numbers requesting OTPs look suspiciously similar or follow sequential patterns (e.g., +1234567801, +1234567802, +1234567803), this isn’t just a coincidence.
Bots often use automated number lists to request OTPs, so spotting these patterns is a clear sign of SMS pumping fraud.
4. Lower conversion rates
SMS pumping fraud can be reflected by your conversion rates. Once fraudsters receive the OTP SMS, they won’t bother following through with it since they already got what they wanted.
If you notice a drop in conversion rate (overall or in a specific country), it’s a strong indicator that fraudulent traffic is inflating your user base without delivering real value.
5. Customer complaints about delays
Fraudsters clogging your SMS system can cause delays for real users trying to receive their verification codes.
If your customer support team starts receiving complaints about slow OTP deliveries, your system may be overloaded with fake requests.
6. Your SMS budget is leaking
Finally, if your SMS budget drains faster than usual or your monthly bill skyrockets without any corresponding increase in user activity, your company has certainly paid fraudsters for a nice holiday.
How to prevent SMS pumping fraud?
Detecting SMS pumping is a first step in the right direction. But now you're probably wondering "How do I prevent fraud before it impacts my bill?”
Here are some ways you can prevent fraud to protect your company and your users.
1. Set a daily balance limit with your provider
One of the most used ways to prevent SMS pumping fraud is by implementing rate limiting. This involves setting a cap on daily message volume or spending thresholds.
For instance, you could establish a policy that your SMS spend should never exceed $300 per day for OTP verifications and SMS-based authentications. This safeguard prevents you from getting hit with a shocking bill at the end of the month or year.
However, handle this carefully. While rate limiting can block fraudulent activity, it can also trigger false positives, preventing genuine users from completing their transactions, especially if your app experiences an unexpected surge in real traffic. Regular monitoring and adjusting limits in line with growth is key to striking the right balance between security and user experience.
2. Build a block list
Creating a manual block list allows you to flag and block users you’ve identified as fraudulent. However, this approach comes with a major downside: it’s reactive, not proactive. You’re essentially shutting the door after the fraudster has already stepped in, and maintaining the list can be time-consuming.
3. Block specific countries
Another option is to block SMS traffic to specific countries, especially if your business doesn’t operate there.
But proceed with caution. This method can frustrate legitimate users in those regions and may result in lost business opportunities. Unless you have strong data indicating fraud from a specific country, we don’t recommend country bans. Precision is key.
4. Use Prelude Verify API
Built directly within our OTP API, our fraud prevention system uses an adaptive machine learning algorithm to assess real-time risk for each login attempt.
Prelude assesses risk signals for every OTP request — drawing from a vast database of phone numbers and fraudulent activity patterns.
For each login or authentication attempt, the system combines your user data with our risk insights to flag suspicious behavior. This means detecting bots, spam, and fraud attempts before they cause damage, without interrupting your genuine users.
If we identify suspicious users, we take immediate action by blocking those numbers, preventing your business from sending any further messages to them. This means no more interactions with fake users and no more money wasted on fraudulent SMS traffic.
For example, we helped our customer BeReal to reduce its fraudulent traffic by 95%, resulting in a 75% reduction in its SMS verification costs.
Example of a blocked SMS pumping attack
Here’s an example of an attack we recently blocked on one of our customers, a European foodtech company.
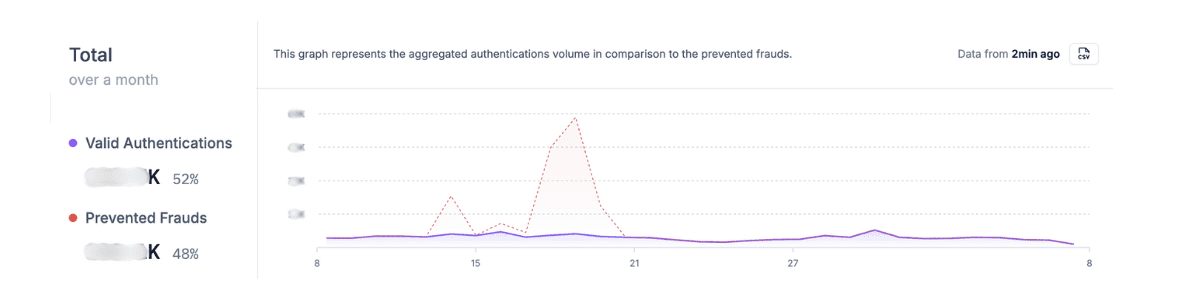
The attack originated from phone numbers registered in the United Kingdom, one of the markets in which our customer operates. While the location wasn’t an immediate red flag, our advanced algorithm flagged an anomaly: dozens of numbers within the same range were showing suspiciously low conversion rates.
Thanks to this early detection, we were able to proactively block these numbers before the attack gained momentum. The fraudulent activity continued for several days, but as soon as the fraudsters realized it wasn’t succeeding, they abandoned the attack.
In the end, we prevented a volume of fraudulent messages nearly equivalent to our customer’s entire normal monthly traffic, saving them several thousand dollars that would have been lost to the attack.
How does Prelude help with SMS pumping?
Prelude protects your business from SMS pumping by detecting and blocking fraudulent OTP requests in real time. Our Verify API uses machine learning to analyze phone numbers, flag suspicious patterns, and stop fake traffic before it reaches your SMS provider.
Through open-source intelligence, strategic partnerships and R&D, we continuously update our blocklist of known fraudulent numbers, preventing you from sending SMS to scammers and ensuring you only pay for legitimate users.
If any suspicious activity is detected, we block the interaction instantly, helping you avoid unexpected SMS bills and keep your conversion rates high.
With Prelude, you get proactive fraud prevention without disrupting the experience of real users.
If you’re ready to protect your business from SMS fraud, sign up for free and start testing Prelude’s API today — no credit card required!
Have questions? Our sales team is here to help. Whether you need more details about SMS fraud prevention or want to explore how Prelude can fit your business needs, we’ve got you covered.
Author

Matias Berny
CEO
Recent Articles


